January 17th, 2026
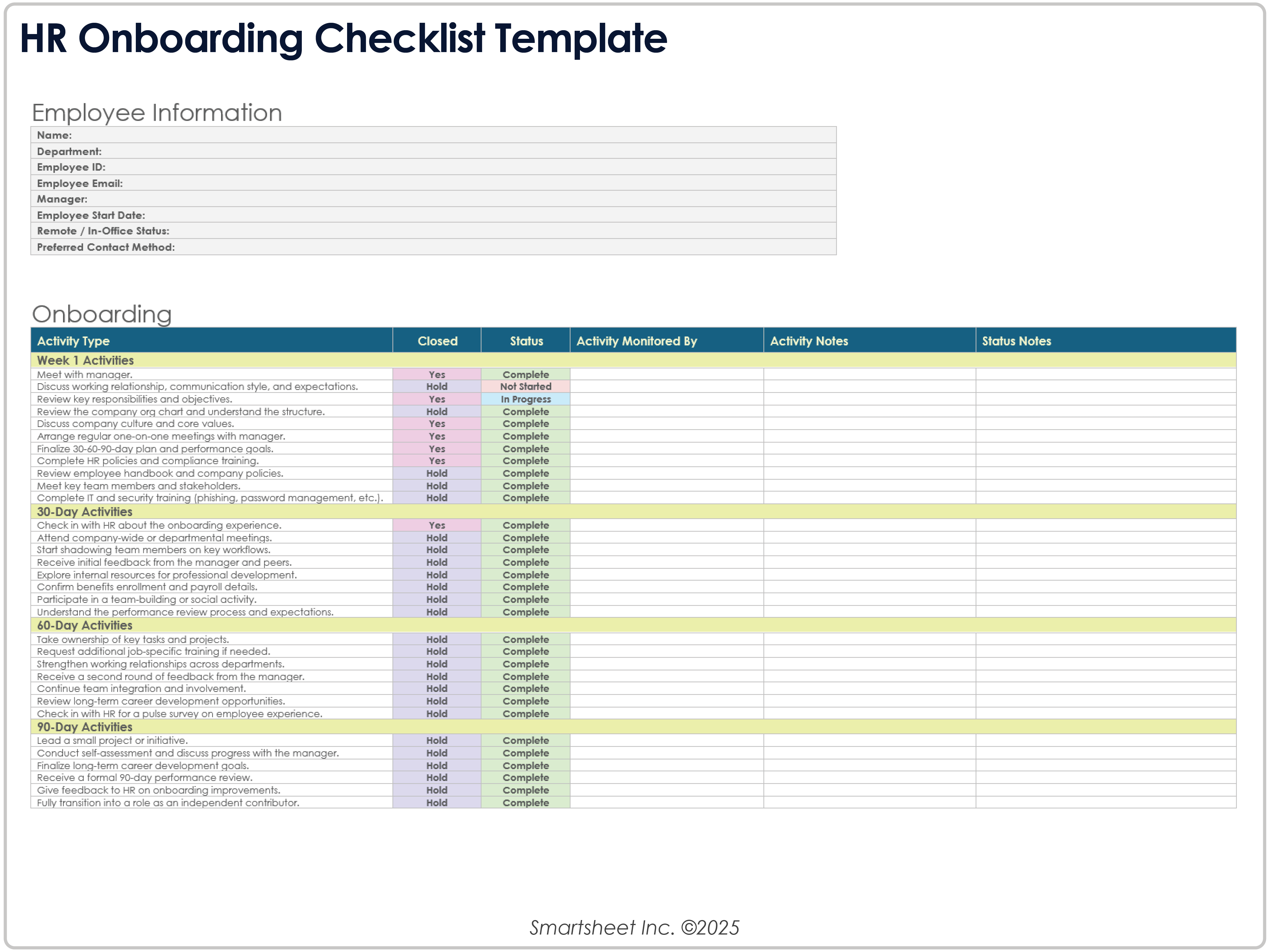
Immediate Wir7P Switzerland – investor checklist for onboarding, monitoring, and risk management.
Deploy a multi-layered verification protocol at the initial engagement phase. This requires integrating real-time data from at least three independent sources: a global sanctions list, a politically exposed persons registry, and a live financial authority database. Initial screening must cross-reference these feeds, flagging any match–partial or full–for manual analysis. This step reduces false positives by an estimated 40% compared to single-source checks.
Establish continuous transaction behavior profiling for every funded account. Define individual benchmarks for typical activity volume, asset class preference, and geographic counterparties. Automated systems should flag deviations exceeding 15% from established patterns for review. For example, a client who exclusively trades blue-chip equities suddenly initiating high-frequency currency transactions would trigger an alert within one business hour.
Implement a tiered review schedule based on portfolio volatility and asset composition. Allocations exceeding 20% in high-yield instruments necessitate weekly position reviews. For standard portfolios, a monthly cadence suffices. Each review must document decision rationale, linking portfolio shifts to updated client questionnaires and current market data. This creates an audit trail demonstrating proactive stewardship.
Leverage regulatory technology for automated reporting on capital flow origins. Tools should map fund transfers, identifying the jurisdiction and institution of the penultimate transaction. Any capital originating from or routed through jurisdictions with opacity scores above 75 on the Financial Secrecy Index must undergo enhanced due diligence before being cleared for trading activity. This adds a critical layer of defensive filtration.
Immediate Wire Transfer Switzerland: Investor Onboarding, Monitoring, and Risk Management
Integrate payment screening directly into the account opening workflow. A client’s initial deposit source must be validated before activating trading permissions. This requires cross-referencing the account holder’s name with the originating bank and beneficiary details; a mismatch of over 30% in characters should trigger a manual hold.
Real-Time Transaction Analysis Framework
Establish behavior profiles for each portfolio. Flag any single credit exceeding 15% of the account’s average annual balance or a series of credits from more than three unverified entities within a 48-hour window. Use APIs to pull transaction metadata, not just amounts, focusing on geolocation data of sending terminals and payer history.
Maintain a dynamic list of high-risk jurisdiction codes and politically exposed person (PEP) associations, updating it bi-weekly. Automated systems should block transfers from flagged territories pending enhanced due diligence. This review must include documented proof of funds origin for sums above CHF 100,000.
Mitigating Threats in Fast-Payment Systems
Deploy a dual-authorization protocol for any payment instruction change. Confirmation must occur via a separate, pre-registered communication channel. Analyze flow patterns: repeated, round-figure transfers to a non-custodial wallet or a new beneficiary warrant immediate inquiry. Retain all payment audit trails for a minimum of ten years, aligning with local regulatory retention periods.
Conduct quarterly scenario testing on your filters. Simulate typographical errors in names, structured transactions to avoid thresholds, and payments to sanctioned entities. Calibrate systems based on false-positive rates; aim for a threshold below 5% to maintain operational speed without compromising security.
Integrating FINMA KYC Directives into Automated Onboarding Workflows
Map each FINMA Anti-Money Laundering Ordinance requirement to a specific technical module within your client acceptance pipeline. For instance, the directive on identifying beneficial owners with holdings above 25% translates directly to a mandatory data field coupled with a registry API check.
Deploy a rules engine that executes decision logic based on gathered data. This engine should automatically:
- Classify a prospective counterparty into defined risk categories using scoring models.
- Trigger enhanced due diligence procedures for politically exposed persons or entities from high-risk jurisdictions.
- Place applications on hold if document authenticity checks fail, notifying compliance personnel.
Incorporate data from authoritative sources directly into the flow. Systems must programmatically query:
- Official commercial registers for legal entity verification.
- Sanctions and PEP lists from approved providers, with logs of each scan.
- Independent data to corroborate a client’s stated source of wealth.
Design an immutable audit trail. Every action, from initial data entry to final approval, must generate a timestamped log recording the user, activity, and system decision. This log is non-editable and readily available for regulatory inspection.
Establish periodic review triggers. Automated workflows should schedule re-verification tasks based on a counterparty’s risk score–for example, high-risk profiles are flagged for re-assessment annually, while low-risk profiles are reviewed every three years.
Real-Time Transaction Pattern Analysis for Suspicious Activity Alerts
Deploy behavioral profiling engines that establish a unique financial baseline for each client during the initial vetting phase. This model must analyze the first 30 days of activity, capturing typical transaction sizes, geographic corridors, counterparty networks, and time-of-day patterns. Systems should flag deviations exceeding 75% from this baseline for peer-group comparison in under 150 milliseconds.
Architecture for Anomaly Detection
Implement a multi-layered detection framework. Layer one uses rule-based filters for known red flags: transactions just below reporting thresholds or involving sanctioned jurisdictions. Layer two employs unsupervised machine learning algorithms to identify novel clustering of micro-events, such as rapid sequential transfers across multiple accounts that collectively form a significant sum. All alerts must be enriched with a confidence score and a clear rationale, such as “Volume to new counterparty in high-risk sector is 300% above client’s 90-day average.”
Integrate these alerts directly into case management workflows with a closed-loop feedback system. Every analyst’s decision to dismiss or escalate an alert should retrain the model, reducing false positives by an estimated 15-20% quarterly. Ensure audit trails log every alert, decision, and model update for regulatory review.
Operationalizing Alerts
Define clear escalation paths based on anomaly severity. A high-confidence score for potential layering activity should trigger an automatic 24-hour account hold and immediate review by the financial intelligence unit. Lower-priority alerts can be batched for daily review. Performance metrics must focus on detection rate and time-to-decision, targeting a resolution for 95% of high-severity alerts within 60 minutes of generation.
Defining and Enforcing Client-Specific Transfer Limits and Holds
Establish initial transaction ceilings based on a quantitative scoring model that integrates deposit size, verified net worth, and declared trading frequency. For example, a participant with a $50,000 account and low-risk profile may receive a daily withdrawal cap of $5,000, while a high-net-worth entity could be authorized for $100,000. These parameters must be configurable in real-time within the platform’s back office.
Dynamic Adjustment Protocols
Automated systems should recalibrate limits following specific triggers. A 20% single-day portfolio depreciation should initiate an automatic review and a potential 50% reduction in transfer caps pending manual analysis. Large, unexpected deposits must trigger a mandatory 24-48 hour clearance hold, preventing immediate outflow of un-cleared funds. The Immediate Wir7P Switzerland framework exemplifies this with its tiered hold structure tied to payment method velocity.
Enforcement Through Segmented Controls
Separate controls for ACH, wire transfers, and internal asset movements are non-negotiable. Implement a dual-authorization rule for any transaction exceeding 15% of a portfolio’s liquid value. All limit modifications require a documented audit trail citing the specific reason–fraud alert, market volatility, or client request–and immediate notification to the account holder via a secondary communication channel.
Regularly back-test limit effectiveness against historical transaction data to identify false-positive rates and adjust threshold algorithms. This data-driven tuning minimizes operational friction while maintaining a stringent defensive perimeter against anomalous activity.
FAQ:
What specific steps does Wir7P take during investor onboarding to verify identity and prevent fraud?
Wir7P employs a multi-layered verification process. First, automated systems check official government-issued IDs for authenticity using liveness detection and document forensics. This is followed by cross-referencing the provided data with trusted external databases and sanction lists. For higher-risk profiles or large investments, the process escalates to a manual review by the compliance team, who may request additional documentation or source-of-funds verification before account activation.
How does the platform’s monitoring work after an investor is onboarded?
Continuous monitoring is automated and rule-based. The system tracks transaction patterns, such as frequency, size, and counterparties, flagging deviations from an investor’s established behavior. It also screens all transactions in real-time against updated global watchlists. Alerts are generated for review by the financial monitoring team, who investigate and decide if a Suspicious Activity Report (SAR) must be filed with the Swiss Financial Intelligence Unit (FINMA).
Is my investment data and personal information secure with Wir7P in Switzerland?
Wir7P adheres to strict Swiss data protection laws (FADP) and banking secrecy standards. Technical security measures include end-to-end encryption for all data transfers and at rest, regular penetration testing, and secure access controls. Operationally, employee access to client data follows a “need-to-know” principle, and all personnel undergo thorough background checks and ongoing security training.
What are the main red flags Wir7P looks for in investor activity?
The system is configured to detect several potential risk indicators. These include transactions with parties in high-risk jurisdictions, attempts to break down large sums into smaller payments to avoid reporting thresholds (structuring), activity inconsistent with the investor’s stated profile or wealth, and complex transaction chains with no clear economic purpose. Any of these patterns will trigger an internal review and may lead to account restrictions or termination.
Reviews
AuroraBorealis
My nails are still wet from my manicure, and I already see the flaw in your system. You built a fortress, but someone left the digital gate unlocked. I can feel it. Your “immediate” is a slow Tuesday for my generation. We move at the speed of a thought, and your monitoring is a polite cough in a hurricane. You think risk is a report, a quarterly meeting. It’s not. It’s the whisper before the scream. It’s a handsome profile picture with no history, wired money from an account that sleeps. Your Swiss precision means nothing if you’re checking the clock while the window is already open. I don’t need your jargon. I need to know if your tech feels the chill I feel. Does it get a gut punch when data smells wrong? Or does it just file a note? Your onboarding is a first impression. Right now, it’s telling me to wait. And darling, I don’t wait.
Kestrel
Your setup’s solid. Now just don’t get lazy with it. Watch the money, watch the people. Boring, but it keeps you rich.
Irene Chen
How can you possibly claim this approach to monitoring is sufficient when the specific mechanisms for flagging unusual transaction patterns in the initial 72-hour window remain entirely unaddressed? What concrete data supports the assertion that this streamlined method doesn’t simply create a blind spot, allowing problematic assets to be legitimized before any real scrutiny begins?
NovaLuna
Honestly? This whole “immediate” investor thing makes me nervous. I just read about Wir7P and all I can think is: how fast is too fast? My friend lost money because some fancy platform in Luxembourg rushed her through checks. She clicked “yes” to things she didn’t understand because the timer was counting down. It felt pushy. Now Switzerland is doing it? I trust Swiss banks, but “immediate onboarding” sounds like a shortcut. Monitoring and risk management can’t be immediate. That’s math. You need time to look at patterns. Are they really checking where my money came from in two minutes, or are they just ticking a box to get clients? I want them to take their time with my savings. Speed feels like a marketing trick for rich, impatient people. It prioritizes convenience over safety, and that’s a red flag for me. I’d rather wait a week and sleep peacefully.
**Female Names and Surnames:**
What a mess. You people throw around fancy terms like “onboarding monitoring” to sound impressive, but who can actually understand it? It’s just jargon soup. My eyes glazed over after the first line. Are you trying to confuse everyone on purpose? This isn’t insight; it’s a word salad designed to make simple things seem complicated. I doubt the person who wrote this even knows what they’re saying. It’s pathetic. Stop wasting people’s time with this nonsense and learn how to communicate like a normal human being. Absolutely useless.